Cyber Security Check-In for Consultancies with Associates
Show clients you take cyber security seriously. An Airtable-based toolkit to help align with Cyber Essentials, flag risks, and prove you’re proactive about protecting data.
Why You Need This
If your consultancy works with associates or freelancers on a BYOD (Bring Your Own Device) basis, every laptop, every phone, every weak password could expose your business.
Clients - especially in the public sector, local government, and corporates - increasingly want evidence that you take cyber security seriously. But contacting each of your associates individually about their compliance with Cyber Essentials requirements? Unrealistic.
That’s where the BYOD Cyber Security Check-In Toolkit comes in.
✅ Gather structured security information from every associate
✅ Instantly flag vulnerabilities and assign a risk rating
✅ Provide AI-driven recommendations and tailored email reports
✅ Track improvements with simple submission dates & remediation status fields
✅ Re-run the check-in bi-annually (or more often) with no extra effort
Not only does this toolkit prove your cyber security credentials, it’s also a gentle introduction to Airtable - one of the most versatile, user-friendly business tools out there which is now powered by AI. If you aren’t already using Airtable in your consultancy, this check-in process will show you its potential for everything from project tracking to CRM.
How It Works
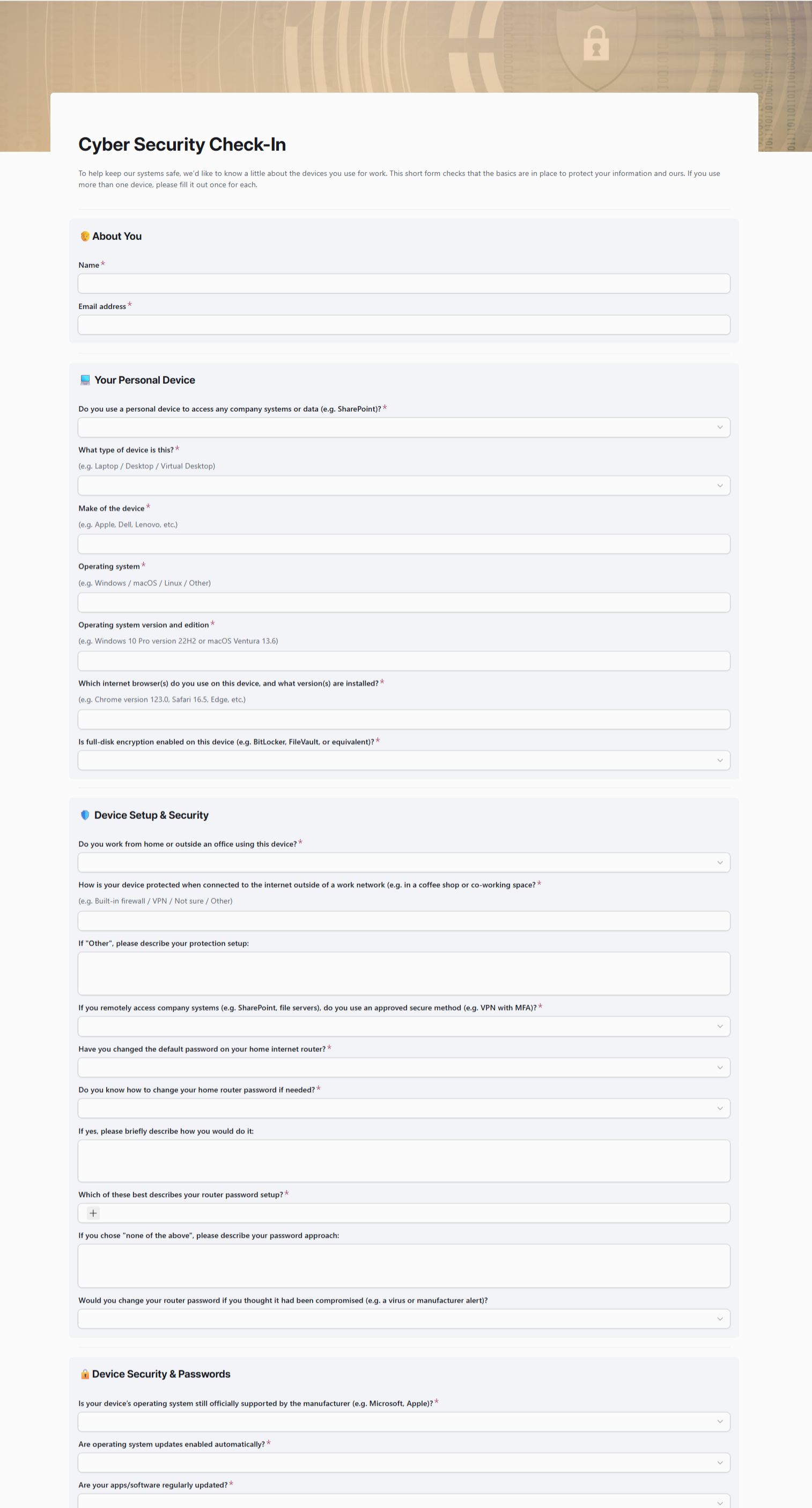
Step 1. Send the form
Invite associates to complete a short cyber security check-in form
Step 2. Collect the data
Each submission feeds directly into your Airtable base — no spreadsheets to wrangle.
Step 3. Automatic analysis
AI reviews each response, flags vulnerabilities, and scores the device.
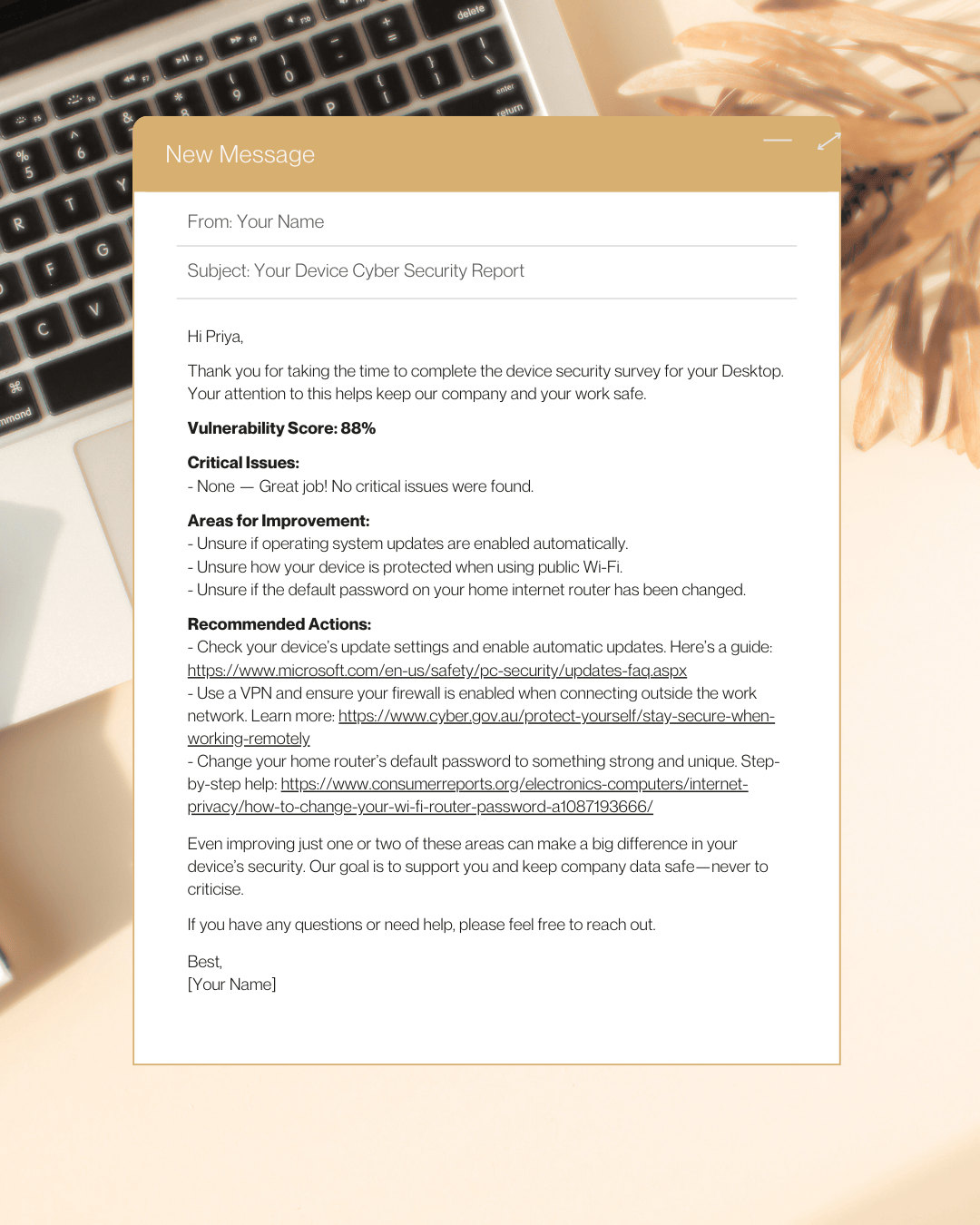
Step 4. Tailored feedback
AI drafts a clear, friendly email for each associate with their personal results and recommended actions, including links to resources to help them improve their vulnerability score.
Step 5. See the big picture
Your dashboard gives you instant visibility of overall security health, overdue check-ins, and outstanding remediation tasks.
Start proving your cyber security credentials today.
Cyber Security Check-In for Consultancies with Associates
Show clients you take cyber security seriously. An Airtable-based toolkit to help align with Cyber Essentials, flag risks, and prove you’re proactive about protecting data.
Why You Need This
If your consultancy works with associates or freelancers on a BYOD (Bring Your Own Device) basis, every laptop, every phone, every weak password could expose your business.
Clients - especially in the public sector, local government, and corporates - increasingly want evidence that you take cyber security seriously. But contacting each of your associates individually about their compliance with Cyber Essentials requirements? Unrealistic.
That’s where the BYOD Cyber Security Check-In Toolkit comes in.
✅ Gather structured security information from every associate
✅ Instantly flag vulnerabilities and assign a risk rating
✅ Provide AI-driven recommendations and tailored email reports
✅ Track improvements with simple submission dates & remediation status fields
✅ Re-run the check-in bi-annually (or more often) with no extra effort
Not only does this toolkit prove your cyber security credentials, it’s also a gentle introduction to Airtable - one of the most versatile, user-friendly business tools out there which is now powered by AI. If you aren’t already using Airtable in your consultancy, this check-in process will show you its potential for everything from project tracking to CRM.
How It Works
Step 1. Send the form
Invite associates to complete a short cyber security check-in form
Step 2. Collect the data
Each submission feeds directly into your Airtable base — no spreadsheets to wrangle.
Step 3. Automatic analysis
AI reviews each response, flags vulnerabilities, and scores the device.
Step 4. Tailored feedback
AI drafts a clear, friendly email for each associate with their personal results and recommended actions, including links to resources to help them improve their vulnerability score.
Step 5. See the big picture
Your dashboard gives you instant visibility of overall security health, overdue check-ins, and outstanding remediation tasks.
Start proving your cyber security credentials today.